When Premier Health care, a physician group based in Bloomington, Indiana, discovered in early 2016 that a laptop from their billing department had been stolen, the loss was far more than just a pricey electronic item. That laptop contained unencrypted patient records – including social security numbers and financial information for 1,769 people, and additional data that could impact more than 200,000 additional patients.
 It’s hard these days to read the news without coming across yet another story of a major data breach at a major organization. The unfortunate truth is that every business today faces the risk of cyberattack – but health care businesses may be even more vulnerable.
It’s hard these days to read the news without coming across yet another story of a major data breach at a major organization. The unfortunate truth is that every business today faces the risk of cyberattack – but health care businesses may be even more vulnerable.
The State of Health Care Cybersecurity
Because of the vast quantities of sensitive patient data and electronic records agencies manage on a daily basis – and because agencies often make the mistake of underestimating their risks and failing to put adequate security in place – they’re frequently prime targets for hackers.
In fact, according to the 2017 Data Breach Industry Forecast from Experian, health care organizations will be the most targeted sector for cyberattacks in the coming years. Almost 112 million health care records were illegally accessed in 2015 alone, and the Ponemon Institute reports that 89% of the health care organizations surveyed experienced a data breach over the past two years.
Health care cybersecurity risks manifest in a variety of ways, including hackers who “break” into Electronic Health Record (EHR) systems via internet connections, thieves who steal either paper records or computers, or even good-old-fashioned human error that makes private information publicly available by mistake.
The Risks with EHR Systems
The FBI claims the value of stolen EHR data can exceed that of stolen financial data. After all, EHRs contain patient names, birth dates, billing information, and policy numbers – all information that can easily be sold or leveraged for significant financial gain.
For instance, fraudsters can use acquired health care information to purchase medications or medical equipment with fake IDs. Others may file false claims with insurance providers. Fraudsters also favor EHR systems because agencies often fail to maintain all available security patches or upgrades. The result is a lax cyber environment, which grants fraudsters the ability to quickly get in, get what they want, and cover their tracks easily as they escape unnoticed.
Most EHRs do include security features, but agencies don’t always properly configure or maintain them. Ultimately, it’s the agency’s duty as part of HIPAA requirements to keep all EHR software up-to-date, encrypted, and properly maintained.
Phishing and Email Scams
“Phishing” emails con victims into giving away sensitive information, such as staff login credentials. These scams can be hard to detect, particularly when the email looks official and the recipient has no reason to believe it’s not legitimate. For instance, the hacker may pose as an IT company asking the staff to update their password after verifying their current login information.
These schemes are typically carried out via email, but they can also take place via social media or even Google Docs. Several businesses in 2017 were caught in a Google Docs scheme, in which victims accepted fraudulent invites to edit documents and inadvertently provided access to their email passwords and address books.
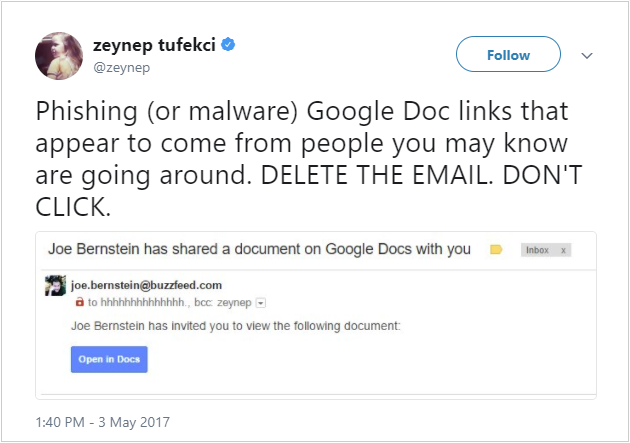
Ransomware and Malicious Software
In 2017, the FBI warned all industries that keep sensitive customer or patient data about the growing ransomware threat, and for good reason: According to Solutionary, 88% of all ransomware attacks in the U.S. in 2016 specifically targeted the health care industry.
Ransomware is on the rise in large part because it works. An attack begins when a victim clicks on a link or opens a document. This sets a potent malware download into action, which locks up the computer and all systems, files, and records until the victim pays a ransom, usually in untraceable bitcoins.
Although ransomware is often spread through phishing emails, it can also spread via innocent-looking links, social media updates, ads on websites, and even trusted software programs such as Microsoft Office.
In May 2017, the entire National Health Service (NHS) in the U.K. fell victim to WannaCry, a relatively unsophisticated ransomware virus that was nonetheless able to spread by targeting a weakness in older Windows computers, as well as computers running newer versions of Windows but that hadn’t been properly updated. As many as one-fifth of NHS trusts, the governing bodies that run British hospitals, were affected.
Employee Risk
Frequently, well-intentioned employees create the biggest cybersecurity risks for agencies. Something as simple as setting a password to “Password,” “QWERTY,” “12345,” or any other commonly used passwords can provide a hacker easy access to sensitive files. Even more common is the practice of posting the password and credentials in a public place – a simple post-it note with login and password sitting on the reception desk is all it takes.
Hackers are also increasingly sophisticated, making it difficult to distinguish between what’s legitimate and what’s phony. Consider, for example, these well-designed hacks:
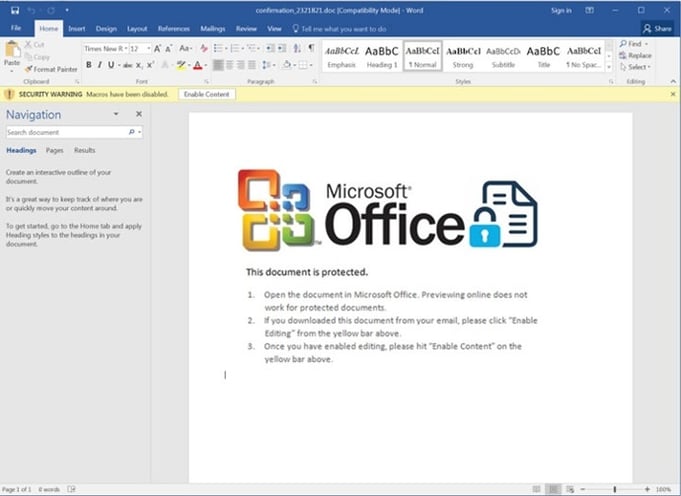
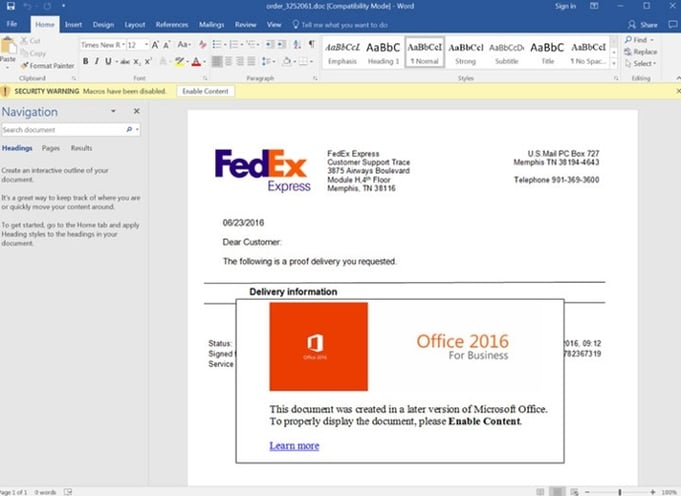
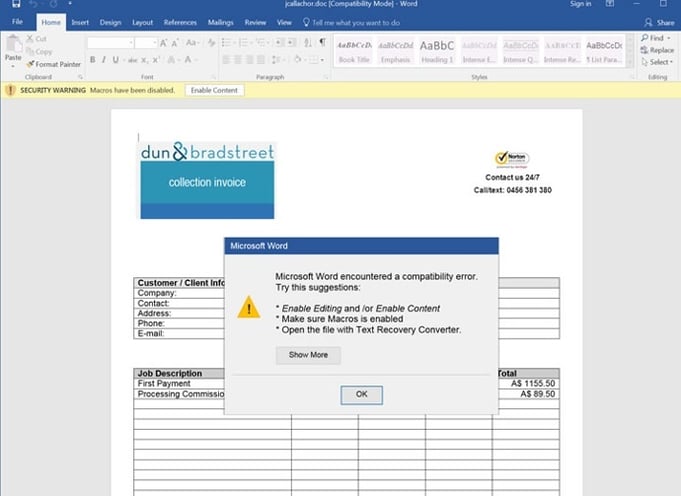
All three are phony – but they’re so well-designed, it’s hard to tell. As soon as an employee clicks on the “OK,” the malicious software downloads, and the agency is in trouble.
How to Avoid and Respond to Cyberattacks
Thankfully, a few simple measures can prevent the majority of the attack methods highlighted above.
Educate Staff on Cybersecurity Best Practices
Effective security largely relies on an agency’s office staff, who typically control the communication systems and points of entry through which hackers may attempt a breach. Office staff and home health workers should therefore be trained to recognize phishing attempts and respond appropriately.
In addition, agencies should discuss and put into place rules or guidelines for keeping information secure. This includes (but is not limited to) the need to keep login credentials private and the need to safeguard the agency’s physical devices, such as laptops or company-issued smart phones and tablets.
Be Vigilant About Staff Authentication
Staff should regularly change login information, and they should always utilize difficult-to-guess passwords that include upper and lowercase letters, numbers, and special symbols. Two-factor authentication can up the ante even further by providing an additional layer of security.
Be Vigilant About Maintaining Software Updates
Downloading patches and updates may seem like a hassle, but it’s a critical step in any cybersecurity strategy. Software providers use these updates to update drivers, deliver bug fixes, and fix security gaps that have been discovered. When agencies fail to properly maintain their software systems, they expose themselves to hackers who specifically exploit the known chinks in the armor with malicious code that targets the unpatched vulnerabilities.
Develop a Business Continuity Plan for Ransomware Attacks
The FBI recommends all businesses prepare for a worst-case scenario. This may include creating an offline data backup system, which will reduce the risk of the agency being held hostage by blocked access to essential records. Should a ransomware attack hit the mark, having backup data may mean the difference between still being able to operate or having to completely shut down.
Final Takeaways
Ultimately, protecting any agency from cybersecurity threats rests in the hands of those who are accessing data on a regular basis. Fortunately, a smart strategy and sound training can go a long way in preventing a successful attack. The right technology can help, as well.
For more information on how CellTrak’s Care Delivery Management solution can help your agency be prepared for any scenario, contact us today.
